Governance Risk Management
Risk Management System
SHAM has stipulated in its Risk Management Regulations the methods of risk management, monitoring the status of risk management, and how to respond in the event of unforeseen serious contingencies, etc.
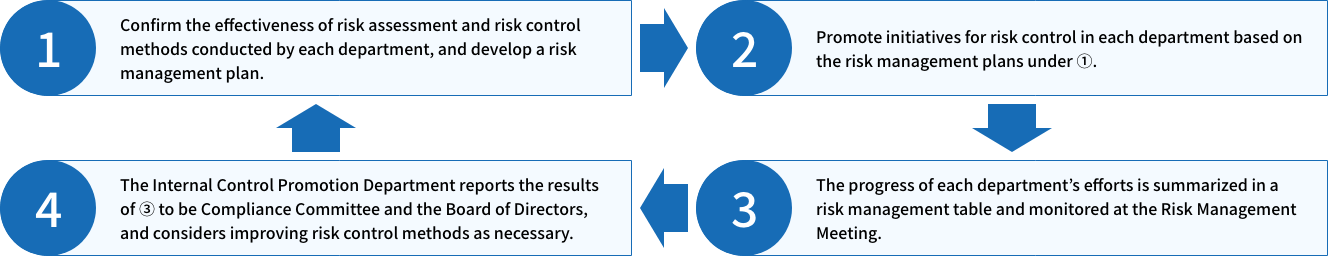
As shown in the cycle below, under the supervision of the directors in charge, each department identifies and assesses the risks facing that department. Each department implements measures according to the risk management plan formulated based on the results for each business year.
The progress of the efforts is monitored semi-annually at the Risk Management Meeting, which is made up of all full-time directors and head of department, and improvement instructions and improvement policies are examined as necessary before reporting to the Compliance Committee and the Board of Directors.
Enhancement of Information Security
To minimize the risks of information leakage, operation shutdown caused by cyber attacks, and other risks that could hinder the continuation of business, the Sekisui House Group strives to strengthen Corporate Governance System about information security regarding the establishment of the group-wide information security governance system as a key initiative, based on "Information Security Policy" regarded as Sekisui House Group's Basic Policy and "Confidential Information Management Regulation".
Click here for the Sekisui House Information Security Policy (Japanese Only).
In preparation for security information incidents such as opening targeted attack emails intended to infect SHAM's computer servers, mobile devices, etc. SHAM has established Response Procedures and conducts drills for directors as well as employees to be prepared for such occasions.
In addition, SHAM established "Information Management Regulations", "In-house Information System Management Manual" and "Mobile Device Operation Manual" as specific guidance for directors and employees, clearly stating information management in daily operations, the proper way to use mobile devices and what to do in case of an information security incident. SHAM strictly manages its information assets by ensuring that employees and directors perform their duties in accordance with these manuals.
Violations by employees or directors of any of the above regulations and manuals, he or she will be punished in accordance with the employment regulations.
